
As mobile phones become critical to our daily lives, there is no surprise that malware is on the rise, hungry to take advantage of lapses from individuals and platforms. Even though spyware is a common predicament for Android users, these are generally not restricted by geographical bounds. However, the latest such malicious software identified by Zimperium Zlabs is not global in scale; in fact, it’s limited to South Korean Android users.
Identified in routine threat research by zLabs, the spying app involving PhoneSpy malware, has made thousands of Android devices in South Korea its victim. The spyware gains access to communications, services, and sensitive data on the compromised device all while hiding from sight in regular lifestyle apps ranging from yoga instructions to apps for browsing photos and video streaming.
Reportedly, 23 malicious apps containing the spyware have been identified, but interestingly, there is no evidence of the PhoneSpy in the Google Play Store. This indicates, that the attackers may have managed to distribute it through third-party platforms or web traffic redirection, though the initial distribution channel is still unknown.
Wherever it’s coming from, once the user installs the malicious app it hides in one of the lifestyle apps and runs perpetually in the background, spying on the user. At installation the app reportedly asks for numerous permissions, if the user misses it, there’s no turning back.
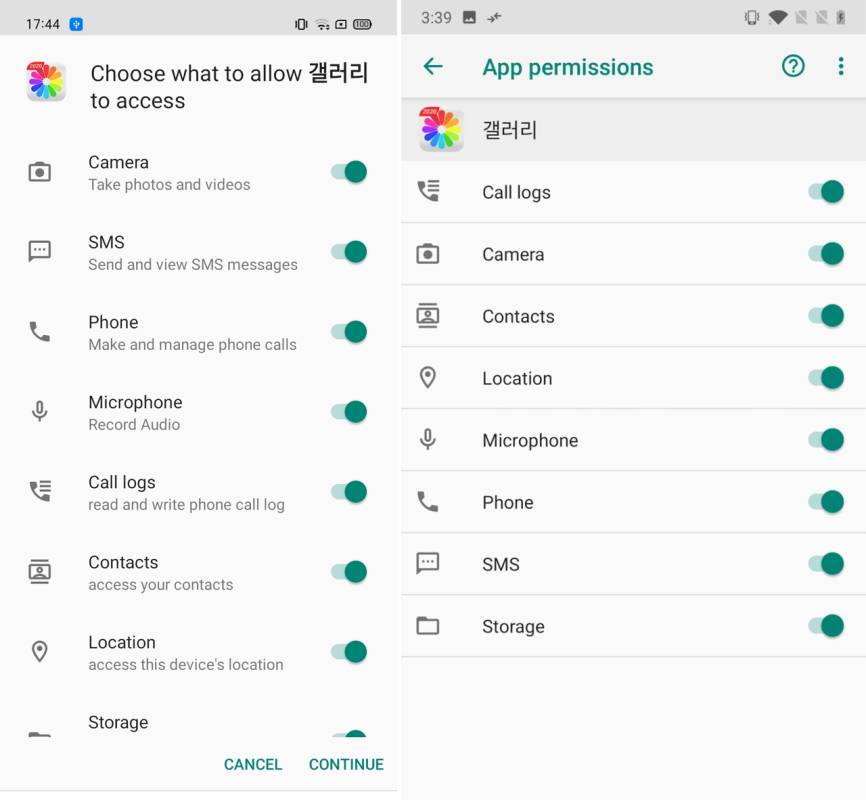
Described as an advanced Remote Access Trojan (RAT), the spyware, in the infected device, steals data, images, messages, and more. It takes control of the microphone and camera to record videos, click pictures, pick up accurate GPS coordinates, and even send SMS messages on behalf of the victim without the users even being hinted of the same.









