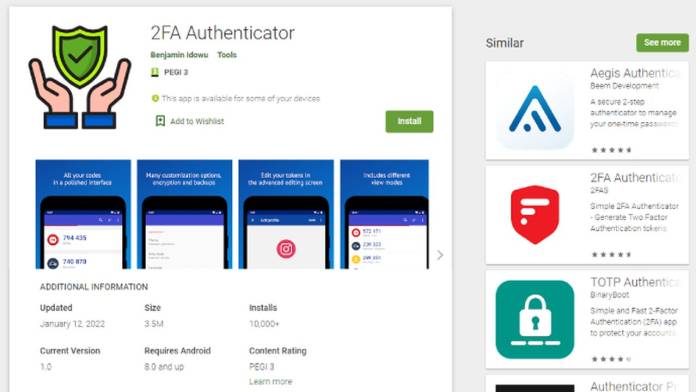
Seems like Google Play cannot shave off its curse of hosting undetected malware apps. In a recent development, an authenticator app going by the name 2FA Authenticator remained under the radar for 15 days on the Play Store and more than 10,000 people downloaded the malicious app capable of stealing financial information. Now the app has been removed, and the cached description portrayed it as a secure authenticator with full-proof encryption and backups. The rogue app is a spin-off of the legitimate Aegis Authenticator; the developers of 2FA Authenticator copied the open-source code and inserted malicious code within.
The app identified by cyber security company Pradeo, also claimed to have support for HOTP and TOTP. This made the users believe it could import other authenticator protocols from apps including Google Authenticator, Microsoft Authenticator, and Authy.
This app managed to pass the Play Store’s security checks, and as soon as it was downloaded on the device, it executed the malicious code. According to Pradeo researchers, 2FA Authenticator managed a low profile and requested critical permissions like biometric access, camera, system alert, and more.

This opened doors for collecting on-device data, disabling keylock and password, installing external apps without consent, and creating overlay windows. Once the app is able to identify a device meeting the right set of conditions – the Vultur, a Remote Access Trojan (RAT) is downloaded.
Thereafter, the trojan keeps on recording keylogs for details entered into the banking apps. This allows cybercriminals to steal money or get full access to cryptocurrency wallets!
Execution by the perpetrators was very precise, they targeted users by location and by gathering the list of installed apps. By fooling the users into downloading the updates, 2FA Authenticator disabled system security checks, and even worked when the app was shut down.
The app was in fact a wolf in sheep’s clothing, slowly draining the unfortunate users of their hard-earned money from banking and crypto reserves. Thankfully, it is ousted from the Play Store and if any one of you has it installed on the device, uninstall it right away and perform a factory reset on the phone to be safe.










Hey there! Just finished reading your article on “Malicious Authenticator App Removed from Google Play Store” on Android Community. Let me start by saying a great job! Your insights hit home for me.
I was alarmed to learn about the malicious authenticator app that was recently removed from the Google Play Store. Your coverage of the issue sheds light on the importance of staying vigilant when downloading apps and being aware of potential security risks. Cyber threats are clear, and articles like yours serve as valuable reminders for users to prioritize their digital safety.
The way you outlined the deceptive tactics used by the malicious app, such as impersonating legitimate services and stealing user credentials, was eye-opening. It’s commendable that Google took swift action to remove the app and protect its users from potential harm. After reading your article, I’m more cautious about the apps I download and will take extra precautions to verify their authenticity. Keep up the fantastic work!
Looking forward to reading more from you.
https://mygs.store/
Great content such a wonderrful experience looking forward to reading more content.
https://www.blogfiliates.com/blogs/the-benefits-of-grooming-your-pet-at-home-by-a-step-by-step-guide