
Last year, the Stagefright bug caused relative panic in the Android world because it was discovered that hackers could access your personal data collect it by going through an unsecure path in Android’s media processing stack. Google had to painstakingly address each one of those many holes in the media stack through monthly patches – with the help of a lot of “white hat” hackers and researchers who went searching for those holes. With the advent of Android N, the mothership is keen to avoid similar mediaserver-related vulnerabilities.
Android’s mediaserver component is responsible for media-related tasks within the operating system. As such, it has access to a device’s camera, microphone, graphics, phone, Bluetooth, internet, and whole lot more. The component actually runs in a sandbox, but the problem is that it still has access to a lot of resources and capabilities. The Android team says that it is not surprising that hackers targeted this particular component to exploit.

For Android N – which, as we all know, will be launching within the year – Android developers have divided mediaserver and its permissions into several components and sandboxes. The redesigned and restructured mediaserver now follows the security principle of least privilege. For example, “the cameraserver may access the camera, only the audioserver may access Bluetooth, and only the drmserver may access DRM resources.”
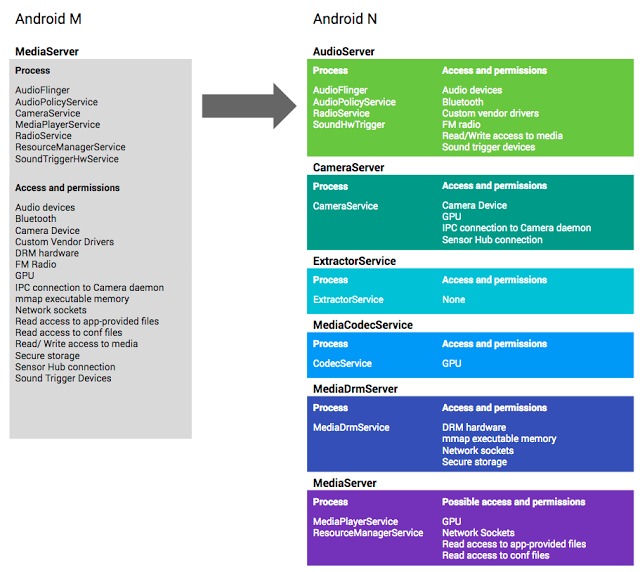
In this new structure, bugs would most likely have access – if any – to a limited component rather than almost the entire device. Android says, “compromising libstagefright would grant the attacker access to significantly fewer permissions and also mitigates privilege escalation by reducing the attack surface exposed by the kernel.” Hopefully, this means a more secure Android for every one.
SOURCE: Android









