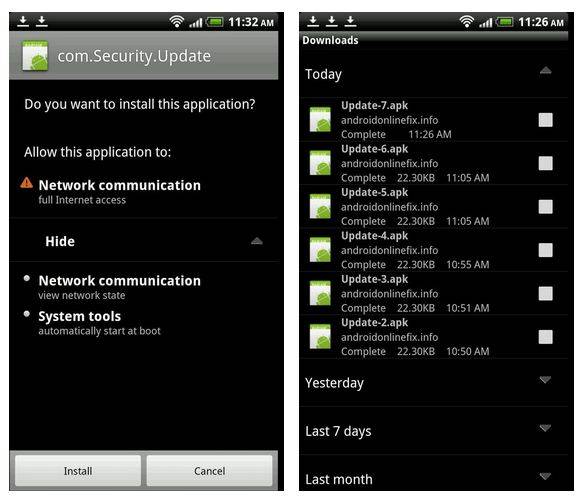
It’s interesting to watch the security landscape unfold on a new platform like Android, in a macabre sort of way. On the one hand we have newfangled attacks that use relatively modern ways of stealing money or information, like phony text message trojans. On the other we’ve got old-school malware that spreads through modified versions of popular software. Now there’s a new trick up malicious programmers’ sleeves, though it’s only new to Android: spreading malware through infected websites.
Lookout Mobile has identified the “NotCompatible” trojan, which hides in the iFrame architecture of some websites and waits for an Android browser to visit the site. It then downloads an innocuous APK file and installs it. At this point the malware doesn’t seem to do anything – apparently whoever’s installing the malicious code is at the testing stage right now. The number of affected sites is small at the moment.
The problem with this particular approach is that it exploits a weakness in Android’s browser itself – no amount of vigilance or care will help if you can just stumble into the wrong website. And since the flaw is a part of Android, phones and tablets will need to be updated to patch the vulnerability. Issues like this illustrate the need for quick, regular update channels for all devices – and why advanced Android users are so frustrated that they often aren’t put in place.
[via SlashGear]










I was using Lookout trial. I deleted it immediately.
Because?
What made you delete it immediately?
You should share why you delete it for the benefit of the android community. Otherwise it only serve to confuse and it doesn’t benefit the forum.