
We talked about the DressCode malware before. It’s malware that takes advantage of an Android device by creating botnets and generating illegal income for hackers via ads. Now security software firm Trend Micro says that hackers are finding other uses for the DressCode malware, and it can compromise the security on enterprise networks.
Basically, the DressCode malware lodged within an app is a Trojan, and once the Trojanized app is installed on a mobile device that connects to an enterprise network, the danger begins. The malware connects to a “command and control” hacker computer and allows the hacker to get access to the network using the mobile device as a sort of tunnel into the network. From there download of sensitive data can be possible, or denial-of-service attacks can be done via the creation of botnets within the network. Here’s an example of an app that has DressCode malware.
The problem is this: Trend Micro says that their anti-virus software has detected over 3,000 apps out in the wild with the DressCode malware. Trend Micro says that over 400 apps in the Google Play Store may be infected with this malware, and that some of these apps have been downloaded over 100,000 times.
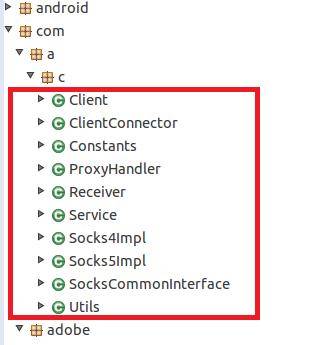
As before, the best thing to do is still to monitor the permissions that an app requires when you install and run it. When game apps or other entertainment apps require network permissions and other critical permissions that are not usually used by games, you may need to uninstall it.
SOURCE: Trend Micro









