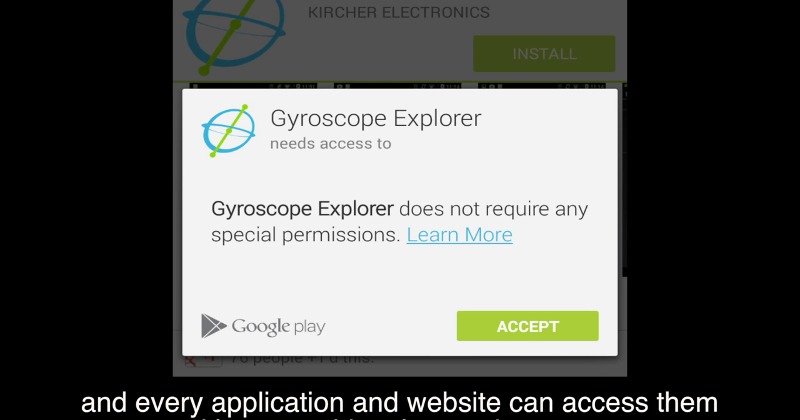
It is almost difficult to believe that a seemingly innocuous part of your smartphone would be a huge security hole, but then again that is how miscreants usually gain unauthorized access to otherwise secure systems. Standford researchers are once again proving how a device’s motion sensors, this time the gyroscope, can be used to compromise your security and spy on you, without you knowing the better.
Last year, it was the accelerometer, responsible for measuring the speed of movement or turning of the device, that was being put under a microscope. According to Standford researchers, accelerometers, as well as microphones and speakers, have unique identifying marks that can be used to monitor the components and, by extension, the devices that house them. All a web service or app needs to do is to store that ID associated with the data coming from the sensor and then watch for that same ID whenever the device access the service or the app.
Now it’s the gyroscope, which is more interested in orientation and rotation, that is on the hot seat. According to Standford researchers and Israel’s defense research group, the sensor can be used to eavesdrop on phone conversations. This is because, according to them, gyroscopes are sensitive enough to pick up sound waves, practically turning them into microphones. The process isn’t perfect but it is enough to probably generate some panic. The demonstration, which is scheduled to be shown to the public at the Usenix security conference this Friday, showed that it can pick up the speaker’s gender with 84 percent certainty, differentiate the owner’s voice from surrounding voices with 65 percent certainty, and distinguish spoken digits also with 65 percent certainty.
Of course, one would first need to install a spying app to be compromised, but that can easily be done by the user without knowing it. The problem is that, unlike other components of a smartphone or parts of a mobile platform, accessing the gyroscope does not require special permissions. Not that majority of users will even read permissions when installing apps, but the lack of a default gate might already be worrisome by itself. That said, there isn’t any reason to panic just yet, as this security hole is still more of a proof of concept. But who knows what may happen once the cat is truly out of the bag.









