There are a lot of uses for Android emulators on a PC system. Some people who work on a PC most of the time but need Android functionality will find a use at one time or another for an Android emulator. One of the popular ones, we believe, is the Andy OS Android emulator. So it is pretty sad to know that the installer for said emulator has been discovered to install a third-party crypto-currency miner without the user’s permission. That makes the installer a Trojan, and is definitely bad for your system.
In a post on Reddit by user named TopWire, the user says that the Andy OS emulator was installing a GPU Miner Trojan without a user’s knowledge. This Miner would be installed in C:\Program Files (x86)\Updater\updater.exe and launches upon the PC’s startup, and would then commence to use up the GPU resources of the computer. One of the main reasons that this installation goes through is that the program is not detected as malware or a miner by popular antivirus solutions.
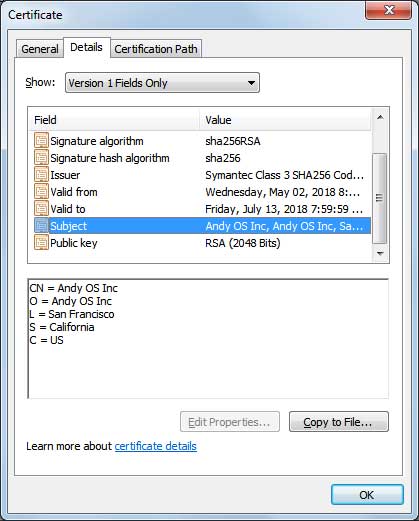
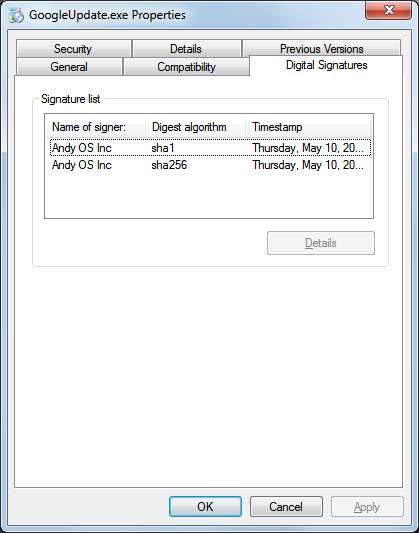
The program itself is not bundled with the installer. Instead, Andy OS emulator calls an IP and then downloads the cryptocurrency miner to your system. According a more in depth analysis of the installation process here, a file called GoogleUpdate.exe will be executed upon running the emulator. When executed with the command line “GoogleUpdate.exe /svc”, the program launches another program named UpdaterSetup.exe, which then installs the miner Updater.exe program and configures it to automatically start when you log into Windows. Check out the video below by the user.
The Reddit user has attempted to contact Andy OS emulator developers but has found himself blocked a number of times from their forums, which is not a good sign at all. That the program would use a fake name like “GoogleUpdate” – which upon analysis is a file signed by Andy OS – speaks a lot of bad things for the developers.
We would recommend that you refrain from using Andy OS Android emulator at this point in time, and wait for official comment from the developers.
SOURCE: Reddit









