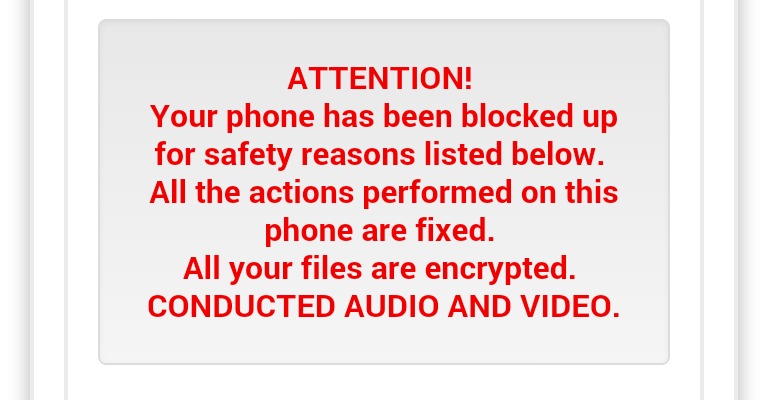
Proving again that mobile security is also only as good as your own vigilance, a new type of Android malware has been unearthed. The Trojan Koler.A holds your smartphone hostage, rendering it practically unusable, until you pay a not insignificant amount of $300.
The victims of this type of malware known as “ransomware” might not all be unsuspecting or innocent, though they could also just be the victims of other people using their devices. It all starts when a user, whether the owner or someone else, visits certain porn sites. This triggers a download of an APK that masquerades as a video player. Should the unwitting, or eager, user choose to bypass Android’s usual security measures and installs the APK anyway, they will then discover that they will be locked out of their smartphones. They will be greeted by a message, crafted to their particular geographical location, informing them that they have been caught red-handed browsing illegal content and, in accordance with certain laws, are prevented from using their device further. That is, until you pay the $300 ransom via untraceable payment services.
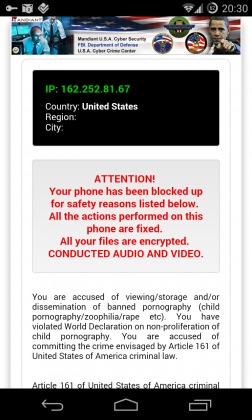
Unsurprisingly, Koler.A is reported to have already duped quite a number of people, 68 in total with 5 coming from the US. The ransomware operates quite simply, in theory. It puts up a browser window that always stays on top of any other app. You can press the home button to get to the homescreen, but after five seconds, the browser will popup again. If you’re fast enough, or if your manufacturer’s homescreen has that functionality, and if the malware app is at the very first screen of your app grid, you can probably manage to have it uninstalled before it triggers the popup again. Otherwise, perhaps only a complete reset or wipe would remove the offending app from the device.
There is, of course, a lesson to be learned here, but it is easy enough for users to fall victim to sometimes even the simplest social engineering and malware combinations. While the Android platform itself can only go so far in trying to keep users safe, with safeguards such as preventing the installation of apps outside of sanctioned app sources, the last line of defense will always be the user.
VIA: Ars Technica










so if you are rooted you just go back to your previous backup and its gone… Seems simple enough to get rid of. But in all seriousness a ransomware that has effected 5 people in the USA is really not news is it?
First 5, next 5000. Knowledge is power.
Just boot to safe mode and delete the app… No reason to reinstall anything!
too bad general users won’t know how to do that x_x
WOW! What suckers!!
I’m glad I’ve rooted and installed CWM. They can’t stop that so easily…