We’ve heard of Hummingbad but didn’t really put a spotlight on the issue. We thought it was just another malware that would easily go away and be erased but unfortunately, it was worse than we imagined. The virus was discovered last February and since then, mobile threat researchers at Check Point have been checking on the malware. An analysis report was recently published, informing the public of the many dangers and what have already transpired.
Check Point said that numbers went up in May and more phones were infected by the Hummingbad. The idea of the malware is to work as a rootkit on Android that can install apps and generate ads. Most of these are fraudulent activities by one group of genius developers that are actually legitimate business people in Beijing.
Interestingly, there’s a team that has been working on the malicious components within Yingmob. The Development Team for Overseas Platform has several groups within. The ‘drive-by download attack’ approach perhaps helped in making the malware bigger. The idea is that others can access your phone to get important details and information but only to sell them to whoever whether hackers or businesses.
Check Point security company shared they monitored the group’s activities to determine how compromises are done to about 85 million phones they control by having their apps installed but a small percentage of the number have the malicious software on their devices.
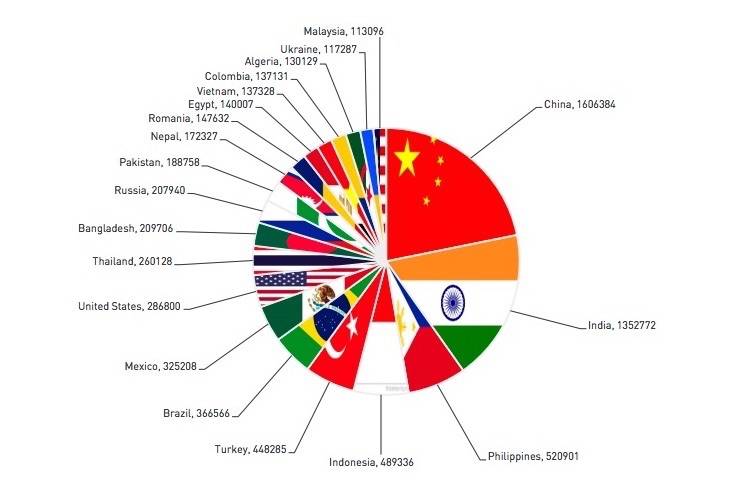
The Chinese mobile ad server Yingmob’s team responsible for the Hummingbad is said to be earning $300,000 monthly average with the malware as made possible by fake ads and forced downloading. It appears to be a very organized scheme to make the malware “go to work”. Based on the research, about 1.6 million in China and 1.35 million in India have been victimized. In Turkey, Indonesia, Philippines, numbers are less than a million Australia and UK have less than 100k phones infected while the United States have about 288K.
SOURCE: Checkpoint









