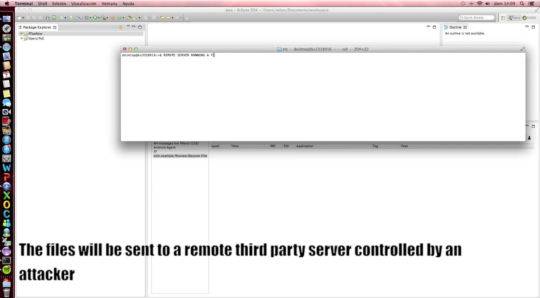
Firefox for Android has an alarming security issue. Developer Sebastian Guerrero Selma has successfully used Firefox to pull data from the storage of an Android device, as well as access the content of privately stored data within the browser.
Browser data, such as passwords and other personal information, can be extracted using the ubiquitous file:// syntax. By visiting a site with the malicious Javascript code, users give up their info to a hacker without ever knowing it. SD Card files, like pictures and documents, are the most glaring example of sensitive information you wouldn’t want anyone to get hold of. Other apps may store info there, though, which could give hackers a backdoor exploit to take further advantage of you.
Selma has notified Mozilla of the issue, and Android Police is reporting that he has sent along a detailed account of how this was done. For a demonstration, check out the video below, in which Selma demonstrates just how he accomplished the info grab.
https://www.youtube.com/watch?v=q74g58kX5lQ
The exploit only works on malicious websites which have the code in use, so if you’re a die-hard Firefox for Android user, be careful where you navigate to. If you’re open to using other browsers, it it could be a good idea for now. Until the exploit is fixed, it’s better safe than sorry.










From similar story reported in Android Police:
Update 2: A representative from Mozilla has
contacted us with a couple of clarifications. We’re told the issue was
fixed in Firefox for Android v24, released on September 17th. It also
seems that the exploit cannot be executed by a remote web page, but must
be activated by loading a local html file or application already on the
device. Thanks, Shannon.
Update 3: Sebastián has been in touch to let me know that his
original work was limited to an app or locally stored HTML file, but he
has since found ways to achieve the exploit remotely. Again, the details
have been responsibly disclosed to Mozilla. Of course, with the
original vulnerability having already been fixed with v24, a remote
attack won’t be very effective.