Hey, security researchers. We appreciate what you do. But the world of malware is worrisome enough without yo giving the bad guys even more ideas. A graduate student at Pennsylvania State University has upped the creepy factor by creating a concept app that can steal keylogging information by surreptitiously reading information from a smartphone’s various sensors, like the accelerometer. The app is called “Taplogger”, and it’s just a proof of concept. For the moment.
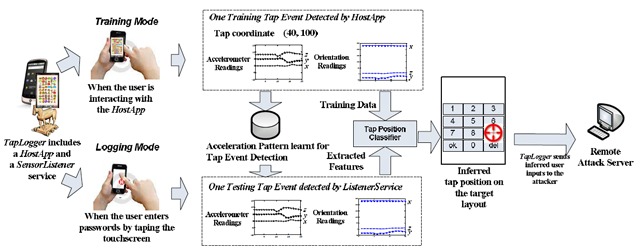
Taplogger disguises itself as a simple memory game, in a manner not uncommon among Android trojans. In the background it records your phone’s movements in three dimensions constantly, waiting for the subtle changes in pitch and yaw that come when a user is inputting a number. It then records the location of a touch on the touchscreen (without ever interfering with a software keyboard or number pad) and “listens” for important personal information, like lockscreen PINs and Social Security numbers.
According to the student who created the app, its intended effect is to illustrate the fact that the permissions for motion sensors on smartphones are dangerously unregulated. The lead PhD candidate notes that the same functions are unsecured on both iOS and BlackBerry, making this sort of exploit theoretically simple. The research paper, “TapLogger: Inferring User Inputs On Smartphone Touchscreens Using On-board Motion Sensors“, was co-authored by University of Pennsylvania PhD candidate student Sencun Zhu and Kun Bai, a researcher working for IBM.
[via Ars Technica]










Not if i use swype…or not?
That’s what I was thinking. It might grab the path, but without interacting with Swype I don’t know how it can determine what letters were used.