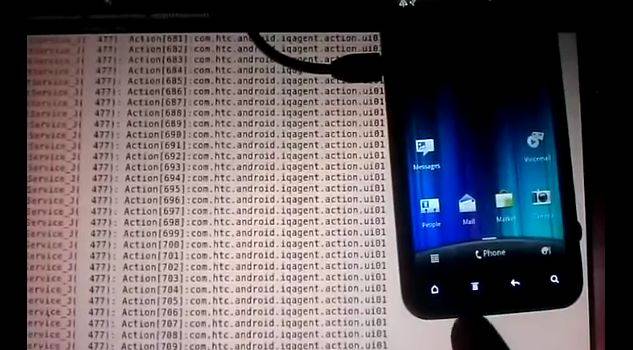
Carrier IQ’s support software has been monitored closely by Android security watchdogs for the last few weeks. After an embarrassing public relations snafu, the company stated that their software does not record personal information, despite the findings of an independent security analyst. But The Register reports that same analyst has now shown the Carrier IQ software logging keystrokes in real time, and transmitting them over an unsecure wireless connection. Carrier IQ is, in a word, busted.
When XDA member Trevor Eckhart published a scathing expose on everything that the software does, including the possible recording and transmitting of location, call data, web history, contacts, used apps and even keystrokes, the Android community was justifiably upset. When Carrier IQ threatened to sue him for exposing theses security and privacy violations, they were, not to put too fine a point on it, pissed. Carrier IQ withdrew their threats almost immediately and placated the public by saying that the software doesn’t record keystrokes or other personal information. That appears to have been a bald-faced lie, or at the very least, an uninformed PR response. Mr. Eckhart has now proven his findings ob video.
You can see an extensive breakdown of the logging process in the YouTube video:
The software is installed on a number of HTC, Samsung, Nokia and RIM (BlackBerry) phones. I’ll point out that the logging and data collection being done certainly doesn’t have any ill intent – it’s designed to let carriers identify and fix problems with their networks. But that doesn’t excuse the massive amount of private information that’s being collected and stored who knows where.
Android Community is attempting to contact the four major carriers in the U.S. to who is using Carrier IQ and on which phones. So far only Verizon Wireless has responded, saying emphatically that they do not use Carrier IQ’s software in any way. we’ll update you with the other responses as soon as they come in.










Is CarrierIQ installed on any of the Nexus devices… like the Nexus One, Nexus S, or Galaxy Nexus?
It’s definitely not on any phone received directly from Google (Nexus One, Nexus S), and it’s highly, highly unlikely to be on a carrier-supplied Nexus device as Google remains the gatekeeper for software updates.
how do you check?
You would need to do something similar to what Trevor Eckhart shows in the videos above (i.e. ADB -> logcat), then parse for a similar process name (like iqagent). No guarantees that it’d be easy to find.
That said, ROM developers are all over the Nexus phones. We would have known about this long ago if it was installed on them.
I used the Andriod Marketplace “Any Cut” app… and did not frin the spyware on my Nexus S. Thank you google!!
This is a massive infringement on privacy. We need answers from all company’s involved.
I’m running CM7 not sure if its in that. Battery is currently flat. If its not there its the ultimate reason to root!
Carrier IQ is not installed in CM7. CM7 is derived from AOSP code (pure, unvarnished Android), which does not have Carrier IQ’s proprietary software. Also, the CyanogenMod team would never stoop so low.
wow this is scary. legal action should be taken.
To clarify, is Verizon saying that the phones they sell do not have CIQ on them, or only that Verizon does not collect the data this rootkit is collecting and sending?
What the video is showing is debugging information that developers can use to see what’s going on in the device. Turning on USB debugging and using ADB is what allows one to view this information. The logcat dump shown in the video is not the CIQ log. They are two very different things.
What the video does /not/ show is what information is actually being logged by CIQ, where that log is, and when (if) that log gets sent somewhere. Does anyone have any more information on the CIQ log?
While this research is impressive I am curious how much is actually valid.
Consider:
No evidence was provided that the information was actually stored. Yes CIQ must attach to the various events to be able to capture the information, and the video shows these events being fired; however it does not show that the data was actually stored anywhere. Talk about glossing over the obvious.
This capability is nothing new, all operating systems have this ability (even your precious Mac OS and Linux). The question is what is done with that information.
Also consider the statement that url querystrings are encrypted when using SSL is blatantly false. Any web developer knows that SSL only protects the body of the request, not the URL. The URL cannot be encrypted and the querystring is part of the URL. If he got this wrong what else is he getting wrong?
If it’s broadcast over an insecure network, anyone with the technical ability can intercept it and use the data however they wish. Duh.
ssl query string are encrypted, google it. So now we must question the validity of your post.
“Talk about glossing over the obvious.”
No Don, it is SO obvious it doesn’t even need mentioning. But Ackhart has shows that it _can_, and that the software _does_ send information in text messages to Carrier IQ. Heck, even CIQ Marketing VP admits it sends information.
Makes me wonder why you feel compelled to defend CIQ…
I really blew that one. Yes querystrings are encrypted at the transport level; but every web browser and web server stores the querystring un-encrypted in their logs. Any expectation that the querystring is secure is false.
Could CIQ decrypt the querystring on it’s own? I am not sure. I am obviously not an SSL expert but I believe the SSL session that is established between browser and server is not just the exchanging of keys. Even if it is why would CIQ go through the trouble when all they had to do was read the logs? The browser might even expose an event that CIQ could attach to programmatically (I know the webview does).
Why am I defending CIQ? Because this is much ado about nothing.
Every operating system in the world has the ability to monitor your activities to this degree. At some point you must trust the OS manufacturers.
How many of you are using an alternative keyboard on your Android device? When you do so you are presented with a dialog stating that the keyboard author has access to everything you type. This is absolutely true. Do you use the keyboard anyway? Of course you do because you trust the keyboard author.
The video is trying to show that you can’t trust HTC and the argument it is using is flawed.
The video starts out by showing that the option to *send* HTC device information from CIQ is turned off. He then shows that even though the flag is off CIQ is still responding to the various events and implies that HTC is lying about the flag. However the video does not demonstrate that CIQ is actually logging or sending this information.
As the developer of this monitoring software CIQ had at least 2 options on how to handle the “send to HTC” flag. The first is to use the the flag to toggle if CIQ attaches to the various events. Had CIQ done it this way there would be no video. However I can see where building the software in this manner could make the architecture much more complex.
A second option, and one that HTC/CIQ have appeared to use, is to use the flag to toggle if the events actually result in the data being logged and sent to HTC. The video does not discuss this option in any way. The video does not demonstrate that HTC is being sent this information.
(I believe the second option is being used because I am a software developer, and the video anecdotally supports this. It appears that there is a CIQ authored background service that is always running and is most likely the same on all devices. There is then an HTC authored component that gets called when CIQ’s component captures an event. It would be up to the HTC component to do anything with that information. This is a logical architecture to use. Again, this is based on what the video is showing and nothing more.)
When the “send to HTC” flag is off does CIQ continue to monitor the various events? YES.
When these events are fired does CIQ actually do anything? According to HTC that would be NO.
And the video does nothing to disprove HTC’s statement.
To all of you asking the about the validity of this….have you all been made into sheep? I dont care if its CURRENTLY sending logs or not…the fact that this software is ON MY PHONE, and there is NOTHING that lets you simply opt out or stop the process is UNACCEPTABLE(and yes i know the noCIQ mod exists but i honestly shouldnt have to go that far). also to “Don Good” you sound like a noCIQ rep. trying to point out things like :
“Also consider the statement that url querystrings are encrypted when using SSL is blatantly false. Any web developer knows that SSL only protects the body of the request, not the URL. The URL cannot be encrypted and the querystring is part of the URL. If he got this wrong what else is he getting wrong?”
Blatantly false? Really?
Yea, I got that wrong, see my reply to Jaap below.
Absolute power corrupts absolutely. We do not know their intent, but we know that their power to spy on us is absolute. Verizon, whom I do not otherwise love, is free of this spyware.
I have 5 phones on T-Mobile and have been searching them all for those unique apps and no single phone of mine has it!
So for whats it worth, I don’t think T-Mo has it either. And 3 of those phones are HTC other is Samsung and LG
Verizon and T-mobile may not be using CIQ; but it would be naive to think that they are not capable of retrieving this information in other ways.
When using any operating system you must assume that all your activity is potentially being captured by the OS. That’s the trade off when you choose when you use the OS.
If Verizon is not using the Carrier IQ information, then why are their Android Phones STILL SENDING the keylogged information to Carrier IQ???? HUH???
shift the blame where it is due…. the carriers.
Blame?
Every OS manufacturer finds themselves in the tough spot of figuring out “how do we support the consumer when something goes wrong.”
Mining the operating system for information to help troubleshoot the problem is an obvious decision.
Microsoft Windows, and I believe Mac OS, ask you at the time of failure if you would like to send this level of information back to the mothership so they can “improve their products.” Instead HTC has chosen to ask just once when you setup the device and then let you change it using a setting.
This video does nothing to prove that HTC is not honoring that setting (responding to an event as shown in the video does not equal using that data).
I don’t see people complaining when an application is logging all activity to help the developer troubleshoot issues with the application.
So why are you complaining when the OS is doing it?
If you really are this paranoid then:
Don’t use alternative keyboards. After all even the OS tells you the keyboard author now has access to everything you type.
Root your phone, oh wait, can you really trust Cyanogen?
I know, don’t use a cell phone.
And while you are at it stop using your desktop, your xbox/ps3, anything with a WiFi connection, your credit cards; the list goes on and on.
Note that I enclosed “improve their products” in quotes above. Even I do not believe this information is being used only to improve their products, but that is a different argument entirely and at some point you are forced to trust the manufacturers to act appropriately or you must chose to not use their devices.
Guys here we are in front of ANOTHER MOST IMPORTANT QUESTION: who is behind this? I mean think just a moment. How is it possible the same “control over the population” software is installed in ALL “COMPETITORS” companies around the world? who is manipulating this information (obviously this “who” is one common dark power) This “tracking” in Android is just nothing at the side of Mac and Windows. But let’s say they do not put any malware in your phone. YOU STILL PASS BY THE SERVERS.Then they still read ALL what you do. I think we have to understand WHO is behind ALL this movement. And they are not the cellphone companies, this is MUCH MORE IN DEEP than just a malware on your phone.