The first line of defense in computer security is the user, or at least that’s the way it works on Android. Whenever you install an APK from the Android Market or via an SD card or download, you’re presented with a list of permissions detailing what hardware and software the app can take advantage of. Wary users often opt to skips apps that take more permissions than are needed, and smart developers often post reasons for requested permissions in the Market. But it looks as if there’s at least one critical flaw in the Android permission system. An R&D director with ViaForensics has proven that the system can be bypassed, by installing an app with no permissions at all that can nonetheless completely control the Android shell.
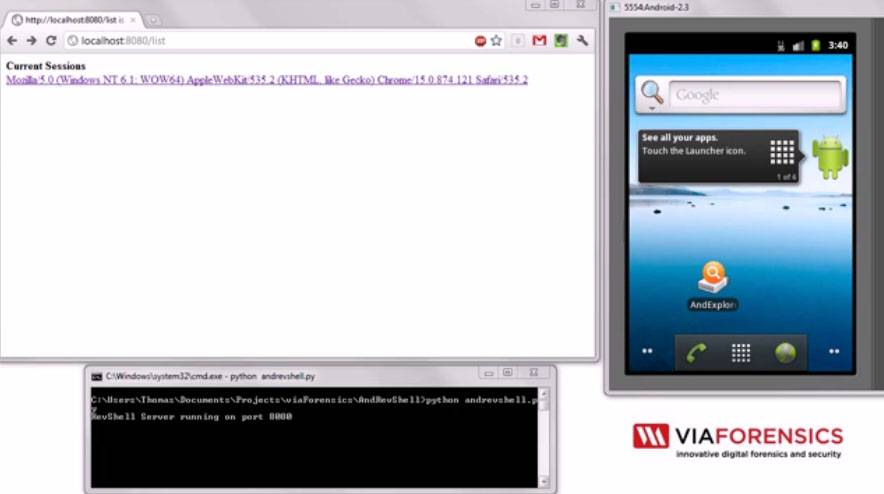
Thomas Cannon demonstrates the vulnerability in a screencasted video, working with a Gingerbread SDK emulator. The app that he’s created installs with absolutely no enabled permissions – it’s about as threatening as a wallpaper, according to Android’s permissions system. The app allows him to take control of the shell via a a remote (virtual) connection. The app displays as “A Game” and requires no security or root access. Cannon says that the exploit he’s using is not new and has been known by security researchers for some time – I’m not knowledgeable enough to confirm or deny this. Cannon says that he’s tested the process on Android versions 1.5 all the way through Ice Cream Sandwich. The app tunnels into the Android web browser to leverage its permissions for web and other access. Other security issues that he found were unencrypted files from the Email app stored on the SD card.
ViaForensics recently exposed vulnerabilities in Google’s Wallet NFC payment system as well. Cannon is a researcher, not a hacker. The application that he’s using is a test APK created to prove the vulnerability. Even so, the demonstration is worrying – if an advanced developer can manage the trick, an intermediate one should be able to figure it out eventually. Cannon didn’t articulate the particular system he’s using to take over the Android web browser, but presumably the engineers at Google can find it and plug the hole. As always, check your permissions (even if they might not tell you the whole story) and only install APK files from sources that you trust.









