
Another month and another headache for Android users as the tarnished banking Trojan “FluBot” again makes an appearance. This time around it is tricking the users into downloading a phony security update that’s actually disguised as malware itself. Ironically, this download will not heal your device in any way, in fact, it will bring more trouble to the Android ecosystem. If you fall for this trick and click on the message, it will install the FluBot malware, which was earlier disguised as a text message.
The malware was discovered by CERT NZ, a New Zealand government agency that alerts users and enterprises about new cyber security threats. According to them, the message is crafted in a way to create panic and urgency to click the link – especially among the non-tech savvy.
Once the link is clicked, the hackers have created the interface in such a way that it instructs them to install apps from unknown sources and allow access to Android Accessibility service on the phone. Unfortunately, this will install the update with the user’s consent.
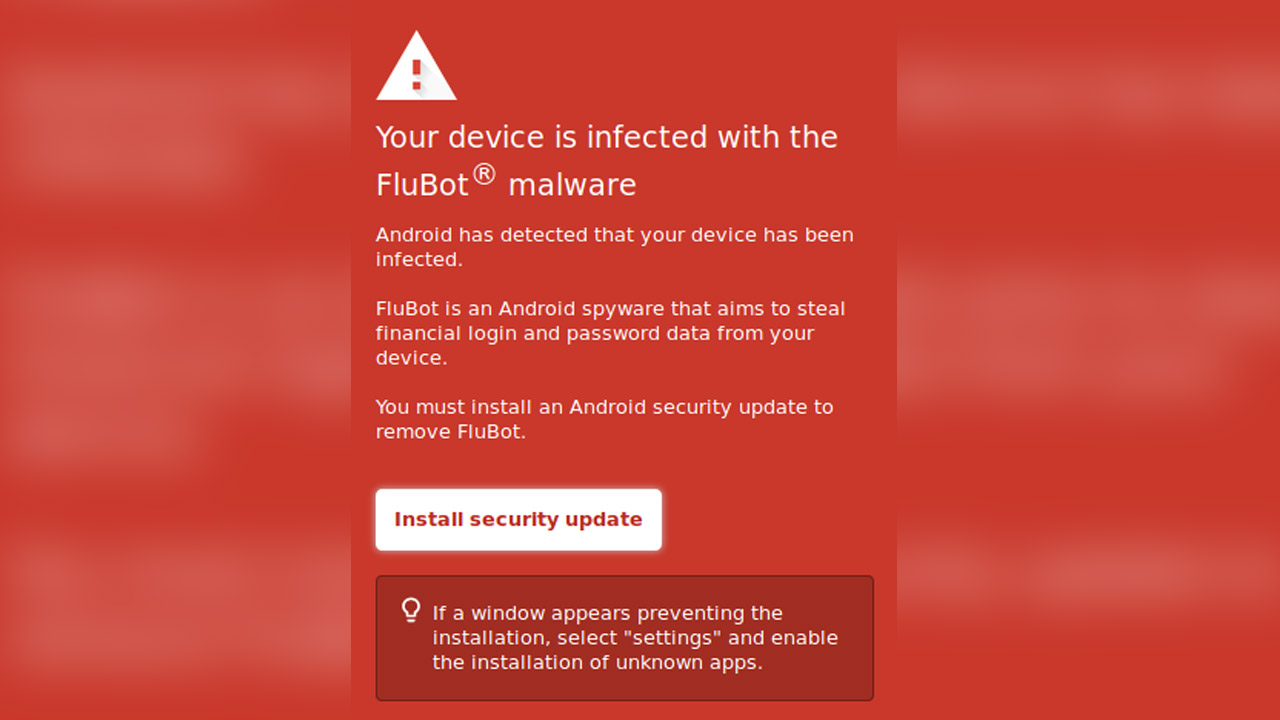
FluBot is quite dangerous as it can track payment and banking information with overlay attacks. Not only this, the malware will gain access to the phone’s contact list to send phishing messages to spread itself to other innocent users.
Initially, the potent Trojan only targeted the Spanish users, but now it has spread its claws in European countries including Germany, Poland, Hungary, UK and Switzerland. Evidence of FluBot has also been found in Australia and Japan which is alarming for Android users.
According to CERT NZ, the only way to stay clear of the malicious application is by closely analyzing any such prompts and not clicking on anything. The only updates that need to be installed are from the phone’s own settings or the ones provided by the OEM’s software.
In case you suspect that already the app has been installed, backup important data and perform a factory reset on your device. And also immediately contact your bank(s) of any suspicious activity in the account(s) linked to the phone.









