
WAP fraud gained popularity in the late 2000s and the early part of 2010 but eventually died out with the advent of modern smartphones. Now the vulnerability is back as the WAP standard is still being used by some telecom providers. Security research experts have identified this critical exploit that’s been targeting the Southeast Asian users by subscribing them to premium-rate phone services, under their nose without any warning or prompt. In simple terms, this Android malware is going to give you a serious headache as by the end of the month you’ll have a hefty bill!
The security risk has been dug out by security firm Check Point who has named this malware WAPDropper. It starts with the download of a malicious app on third-party app stores that contains the dropper module which is small in size to go undetected by protection tools.
Then this dropper module starts to download the main WAP fraud dialer component without the user’s consent. Once the intelligent malware is downloaded (can by-pass CAPTCHA challenges), it signs up the user for premium phone number services from authorized telecommunications providers in Malaysia and Thailand.
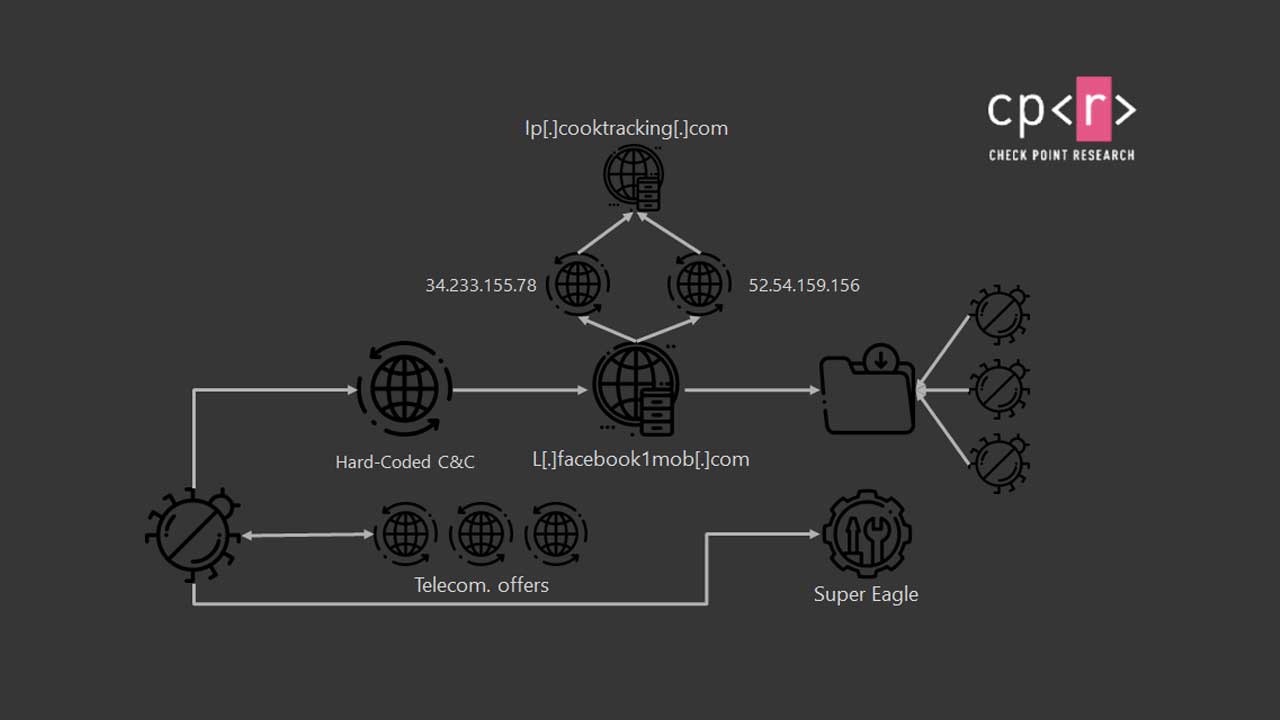
The scam also known as, International Revenue Share Fraud (IRSF), then unfolds as more calls to premium numbers means more dollars added to the bill. Cybercriminals either identify the premium number owners or collaborate with them to mint profit illicitly. In the end, it is the unassuming user who suffers at the hands of these fraudsters.
The apps in unofficial Android app stores that have been identified to have the malware app include af, dolok, Email, and Awesome Polar Fishing. If you have installed any of these apps outside of the Play Store, uninstalling them ASAP is a good idea. Checking your banking statements and phone is also advised if you have these apps installed.
Aviran Hazum, Manager of Mobile Research at Check Point warns that the malware could become more stealth and potent in the future. So it makes even more sense to stay away from third-party stores and only stick to Google Play Store.









