
As much as we love Android, Google’s very own mobile platform needs to be checked once in a while. The tech giant has major efforts to improve on safety, privacy, and security but sometimes, hackers can be real geniuses. It is our duty to share with you what happens in the background ordinary consumers may not know of and that includes possible vulnerabilities brought about by malware and other forms of viruses targeting Android devices. The latest we’ve discovered is Triada. It’s actually a family of viruses that is bringing malware to Android smartphones the past few years.
A case study has been done in the past few years. Google is sharing details that explain how early versions of the malware worked. Google said that as early as at the factory, Triada has been trying to get into phones. Even before the phone is out from the box or before a user can install an app, Triada is present already.
Google researchers are confirming the information that Triada has been sending spam and displaying ads by employing a kit of tools that clearly could bypass security protections. Android has built-in security measures but apparently, they’re not enough.
The malware is said to be powerful enough that it could tamper installed apps especially third-party ones. Triad is described as able to connect to over a dozen command and control servers.
Google confirmed the report and shared this statement:
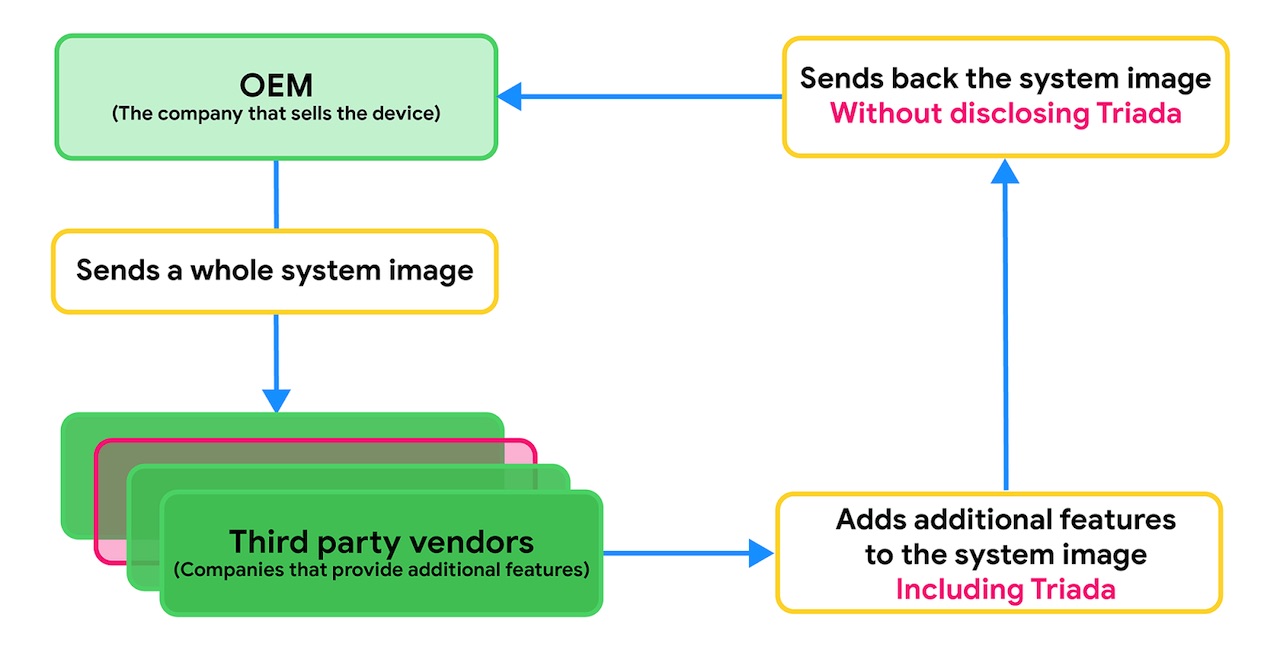
Triada infects device system images through a third party during the production process. Sometimes OEMs want to include features that aren’t part of the Android Open Source Project, such as face unlock. The OEM might partner with a third party that can develop the desired feature and send the whole system image to that vendor for development.
Based on analysis, we believe that a vendor using the name Yehuo or Blazefire infected the returned system image with Triada.
So it’s real. Experts have confirmed the security problem and discovered Triada built into the firmware of other Android devices via a backdoor of one of the OS libraries. This is considered a supply chain attack and many have fallen victim to it.
Triada is considered sophisticated but it’s nothing that cannot be fixed or deleted. It’s advanced alright, showing a lot of adware. Google is doing everything in its power to prevent such vulnerabilities by trying to beat the backdoor and implement improvements in the Google Play Protect system. Google has also started working with OEMs to make sure the malicious app is deleted from the firmware image–to be sure.









