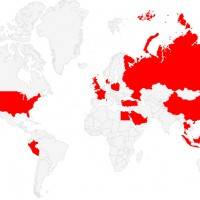
Aside from StageFright which was recently followed up by StageFright 2.0, there’s another threat to Android security. If you ever come across Kemoge, that’s the one–a new malware that is currently bothering a lot of Android devices in over 20 countries worldwide.
This malware was recently discovered by mobile researchers from FireEye Labs, the same guys who said there are new ways to get fingerprints and hack Android phones. This malicious adware is dangerous because it has the ability to takeover the device according to the researchers who also gave it its name: Kemogo. The name Kemoge was just lifted from aps.kemoge.net–the command and control (CnC) domain they spotted.
FireEye has shared a few information about Kemoge. Everything they know, they illustrated in a report. Here’s what we learned so far:
• more than 20 countries have been victimized already
• victims include large-scale industries and government agencies
• malware is disguised as a popular app
• some examples: Sex Cademy, Assistive Touch, Calculator, Kiss Browser, Smart Touch, ShareIt, Privacy Lock, Easy Locker, 2048kg, Talking Tom 3, WiFi Enhancer, and Light Browser
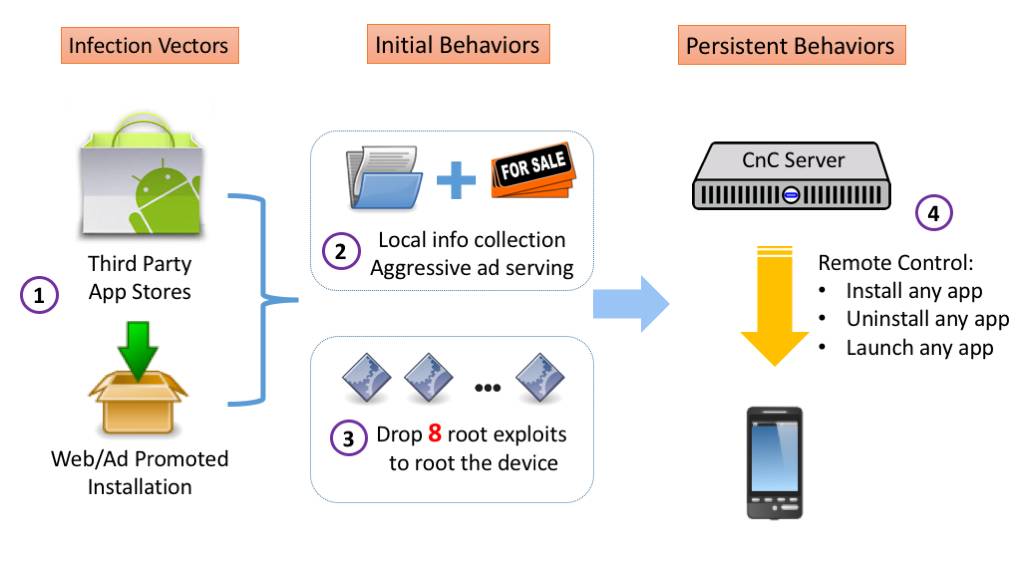
FireEye labs also presented the lifecycle of Kemoge. Usually, the process starts with the fake app being uploaded to the app store complete with download links via ads and websites. When an Android user sees the ad and is enticed, he’ll download it and then end result–malware installed. And so what? What can it do to your phone? It can register MyReceiver in AndroidManifest to launch automatically when connection is changed or when device screen is unlocked.
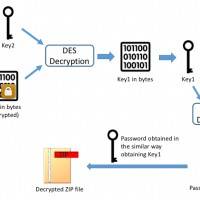
The Kemoge will then do a number of things within the device including generate the ZIP protecting password, extract some files, encrypt some keys, carry several root exploits to root phone, and more. It’s a long process really, but the main point of Kemoge is to upload device information and then do the following: uninstall designated apps, launch designated apps, and download and install apps from URLs given by server.
The malware is still out there. It’s actually a malicious adware family assumed to have come from China. FireEyes Labs shared suggestions on how to avoid this specific malware:
1. Never click on suspicious links from emails/SMS/websites/advertisements.
2. Don’t install apps outside the official app store.
3. Keep Android devices updated to avoid being rooted by public known bugs. (Upgrading to the latest version of OS will provide some security, but it does not guarantee that you will remain protected.)
The group also suggested to use FireEye MTP as a mobile security solution. Make sure you scan WiFi traffic especially if you are using NX appliances. This way, you may know that there are no other devices or possible attackers “lurking” in your network.
SOURCE: Fire Eye











If its third party app stores, please don’t use the graphic for Android Market. Its a bit misleading to people unfamiliar with Android.