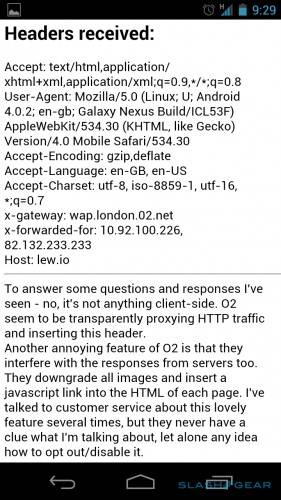
UK citizens who use O2’s wireless network got a nasty shock this morning, when reports around the web claimed that their phone numbers were being exposed to any website they visited from their mobile phones. While not a malicious attack, a setting in O2’s network was broadcasting its customers phone number in addition to standard browser data like user agents, device type and screen size. This morning Android phones and other O2 devices stopped broadcasting mobile phone numbers, indicating that the security hole has been patched. O2 still hasn’t spoken publicly on the issue.
Tech-savvy customers were understandably upset – according to a proof of concept site, any website with the right settings could harvest a significant amount of personal phone numbers without breaking any law, or even going to too much technical trouble. The blunder comes at a sensitive time for mobile carriers, as the privacy faux pas of Carrier IQ and its extreme data logging is still fresh in the minds of the public. Though there’s still no word from O2’s corporate arm, they did tweet a UK security researcher saying that the phone numbers embedded into the HTML code were designed to indicate that the browser was coming from a mobile device. There are many other ways of achieving this determination from a website owner’s perspective.
When questioned about the issue, the United Kingdom Information Commissioner’s Office said that the events did not constitute an official data breach, according to Paid Content. A phone number alone isn’t personal enough to meet the state’s requirements. Even so, a representative said that the organization would be speaking with O2 on the matter, since most people do not expect their cell phone number to be exposed simply by visiting a website.
UPDATE: O2 has shed some light on the issue in an official post on their blog. According to the published information, routine maintenance on the network caused a minor change that exposed some users’ phone numbers for approximately two weeks. the carrier apologized for the error and offered up a Q&A for concerned customers.
[via SlashGear]









