Fact: Viruses and malware abound. Android as a platform is a common target of these genius hackers particularly those living in China. We’re not pointing fingers here but a group of Chinese hackers recently made millions of dollars from spreading a Trojan known as ‘Ghost Push’.
This virus was first discovered by CM Security Research Lab one month ago. The Android community was given a warning about its danger. Apparently, it’s more than just a virus. More variants were found and the viruses were actually part of an illegal mobile marketing industry chain.
So this virus is more complex than it seems. Cheetah Mobile Security Research Lab experts discovered the operations that involved different vendors. We don’t have enough information about whoever is running this thing but about 900,000 Android devices all over the world were affected. That’s almost a million of victims and because money is involved, it is assumed that the developers of ‘Ghost Push’ are making millions every single day that the virus is still out.
That ‘Kemogo‘ virus we exposed just last week is in fact a variant of this ‘Ghost Push’. The malware was discovered by FireEye labs, usually disguised as a popular app. There was also a mobile malware found in Braintest app on Google Play Store a few weeks ago.
We’re not certain if the ransomware for Android discovered by ESET researchers is connected to this virus family but whoever made that malware definitely made some money too.
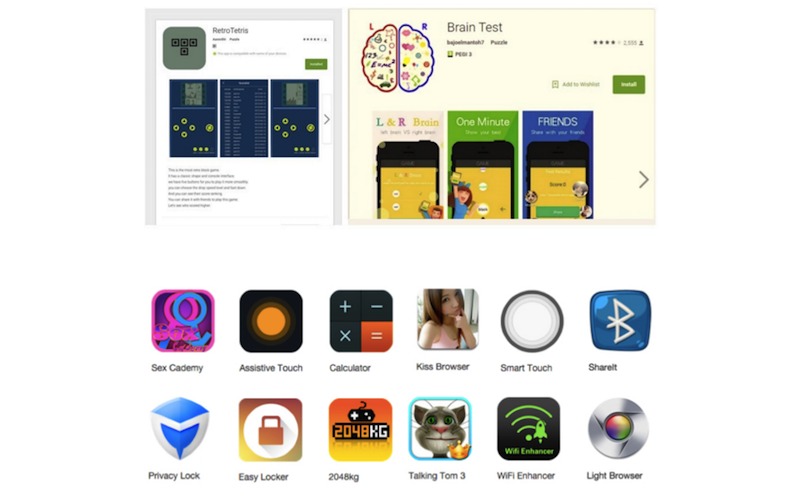
Several malware, different variants of a virus, are spread almost the same way. A virus is repackaged as a popular app complete with malicious codes. It is designed well to bypass security measures so one can still be found on the Play Store and other app markets as a legitimate app. Ads are used and posted everywhere to promote the app.
CM explained how the illegal industry was established. Since most of the malicious apps are difficult to uninstall, the virus developers got a database of active users. Unknowingly, these Android users became part of a user base presented to ad sponsors by some illegal marketing promotion company.
Here is an illustration how this mobile dealers are doing the illegal operations:
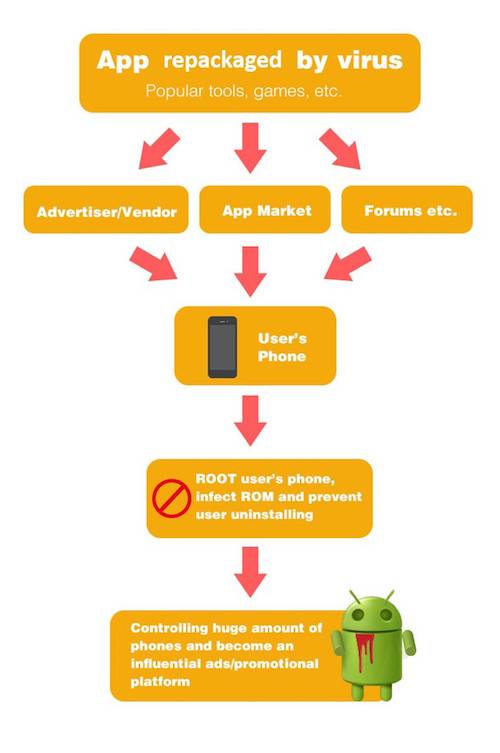
It seems very simple now. And just like FireEye Labs, CM Security analyzed the command and control (CnC) domain of the virus and found out four domain names involved: GhostPush, GhostPushII, OIMobi, and Kemoge.
CM Security also said that most of the victims are concentrated in Southeast Asia for the obvious reason that China, where the viruses originated, is near the region.
Here are some more highlights of the report:
• Almost all Android versions have been affected–from 2.3 to 5.1.
• Top 5 regions affected: India, Indonesia, Mexico, Philippines, Russia
• Regions LEAST affected: USA, Nigeria, Bangladesh, Pakista, Colombia
• Number of daily infections in major countries (estimate): India (below 159,000), Indonesia (125K), Mexico (39K), Philippines (35K), Russia (32K)
• More than 10,000 phone types and 2,742 brands were affected
• Top 10 Brands affected: Samsung, Lenovo, Alps, Micromax, Xiaomi, Huawei, OPPO, HTC, TCT, LGE
• 93 apps have become victims of being promoted maliciously by the viruses
• Virus developers can make over 4.05 million dollars from this illegal industry chain every day – CM Security
As a solution, CM Security Research Lab presented a special app as a security tool to target the virus family. CM Security and Clean Master partnered and worked on this ‘Ghost Push Trojan Killer’. The app is described as the first tool that can kill the stubborn Trojans. It’s the first in the world targeting such malware.
Download the Ghost Push Trojan Killer from the Google Play Store
SOURCE: CM Security



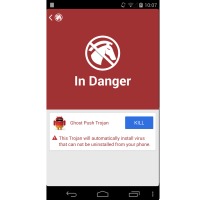
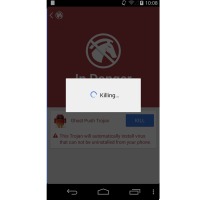








When did this CM security research Lab launched this Stubborn Trojan Killer app?? please reply asap 🙂